THE ESSENTIAL GENAI VISIBILITY, INSIGHT AND
AI TRiSM PLATFORM FOR GENAI STRATEGY LEADERS.
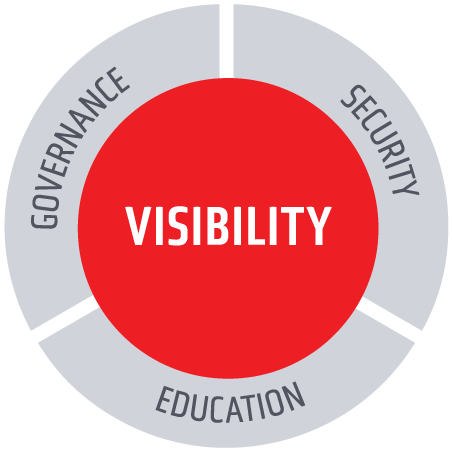
Learn to embrace and accelerate Generative AI securely
and responsibly with our Visibility, Security, and Governance platform.
The question is not whether you can afford to get visibility into your GenAI usage, but whether you can afford not to.
"Generative AI. It’s at once a game changer, and an enigma. Not just in terms of massive potential,
but also in driving realizable economic returns, orchestrating organizational processes and people, and securing and guard railing it."

Sanjay Srivastava
Chief Digital Officer, GENPACT
“Visibility is table stakes for building out any AI program… it allows the CISO to quantify what is going on so they can figure out a strategy. It becomes the genesis for how you solve the problem in the organization.”

Tyson Kopczynski
CISO
"Security for Generative AI capabilities requires a different approach – we have to rapidly enable our people to reap its rewards in productivity while reducing the new and unique risks Generative AI creates."

Beth-Anne Bygum
SVP/CISO, Q2
YOU CAN'T UNLEASH
WHAT YOU CAN'T SEE.
INGENUITY BUILT ON UNRIVALED VISIBILITY.
Portal26 is the foundational solution for organizations who want to accelerate their Generative AI program to improve productivity and competitiveness. Our real-time visibility into enterprise wide GAI use becomes the touchstone for benchmarking, strategy, governance, security, monitoring and education.

Responsible AI is Built with
Responsible Data
Apply granular data privacy controls to data training data and pipelines. Use the industry’s richest data security and privacy platform to retain encryption while selecting and extracting model training data from production data.

















Stay Ahead of The Curve on Generative AI
Leverage these useful reports and blog posts on how to rapidly,
responsibly and securely enable Generative AI in your organization.

Download Our Latest Gartner Report
4 Ways Generative AI Will Impact CISOs and Their Teams
News

News
IBM Protects AI From Being Swayed by Bad Data
April 2024
XTraw AI: Machine Learning and AI Applications Podcast
Podcast
#81 AI roundtable: Enterprise AI ethics, governance and safety.
March 2024

News
Lab Coats To Leadership: A Celebration Of Women In STEM
March 2024

News
The Danger of Unmanaged AI in the Enterprise
March 2024