Security For Object Stores
Securing Object Store Data From Ransomware, Data Breaches, And Insider Attacks
Are you worried you could be hit with a ransomware attack and lose valuable data? Are your customers worried large amounts of their data could be compromised from your cloud object stores such as AWS S3, Azure Blob, and GCS? Portal26’s Cloud Data Protection Software provides always-on encryption to keep cloud data secure from compromise and also enables HYOK (hold your own key) to give security control back to data owners.

Object stores like Amazon S3, Azure Blob, and Google Cloud Storage are among the top breached systems of all time. These systems are so powerful and versatile, with a broad range of configuration options, that more often than not customers end up misconfiguring these, and leaking valuable data. In addition, many do not offer the granularity or flexibility to manage cloud data protection at the file level. This means that admin access to these buckets yields massive amounts of data and consequently any type of admin or privileged compromise can lead to disaster.
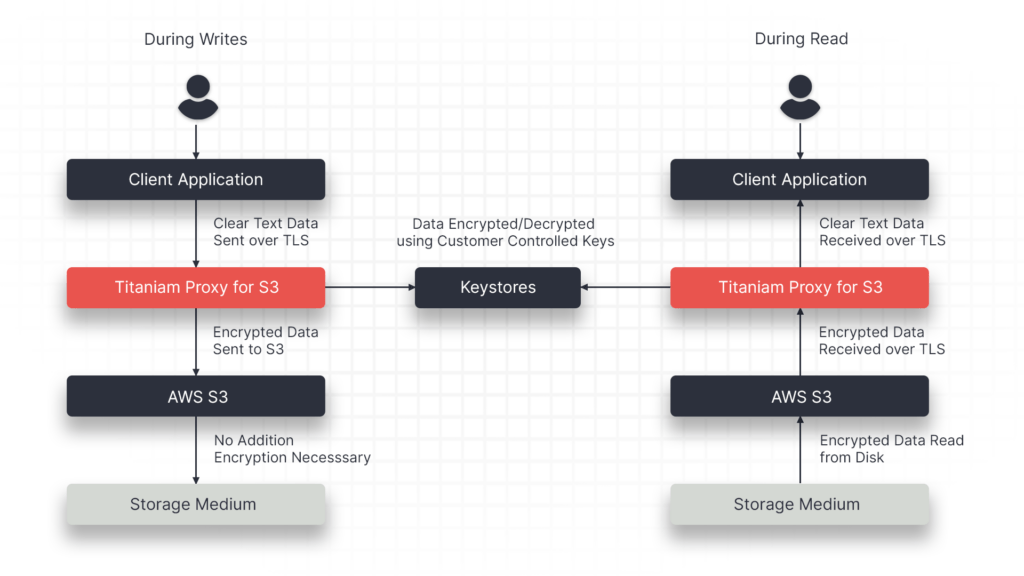
Portal26 provides enterprises with a Cloud Data Protection Software, Proxy, that enables strong and versatile protection for object stores such as Amazon S3, Azure Blob, and GCS. The Portal26 Proxy automatically encrypts all data written into S3 or Azure Blob using NIST FIPS 140-2 validated encryption. Portal26 also automatically builds an encrypted search index with associated metadata. In addition, for structured data, Portal26 also makes encrypted data richly searchable without decryption.
Data that needs to be retrieved from object stores leaves via the Portal26 Proxy and can be released according to granular privacy policies, in a number of privacy preserving formats, and per existing RBAC.
Finally, Portal26 enables rich key control allowing external data owners to either supply encryption keys (BYOK) or hold their own keys (HYOK) for their portion of data on the shared platform. If desired, customers can turn keys off and disable the use of their data.
“With the growing importance of data privacy, the fact that vast majority of data breaches taking place with valid credentials, and the need for companies to do a better job, Portal26 fills an important need to protect data while it is being used”
– Amit Jasuja
Venture Capitalist, Cybersecurity Thought Leader
Portal26 Object Store Proxy Key Capabilities
Portal26’s cloud data protection platform enables both enterprises that use object stores directly, as well as those that have built products on top of object stores, to keep very large volumes of data secure from insider threats, malicious attacks, and data privacy violations.
Portal26’s cloud data protection solution offers security that goes beyond native cloud platform options as it secures against not just cloud platform admins, but also any privileged users or compromise that takes place within the enterprise themselves.
The following are Key Capabilities for this Portal26 Cloud Data Protection software module:

Seamless Encryption

Eliminate Attacker Leverage

No Unauthorized Browsing

Granular Keys, BYOK/HYOK
Searchable Encryption

Enhanced security beyond native platform encryption

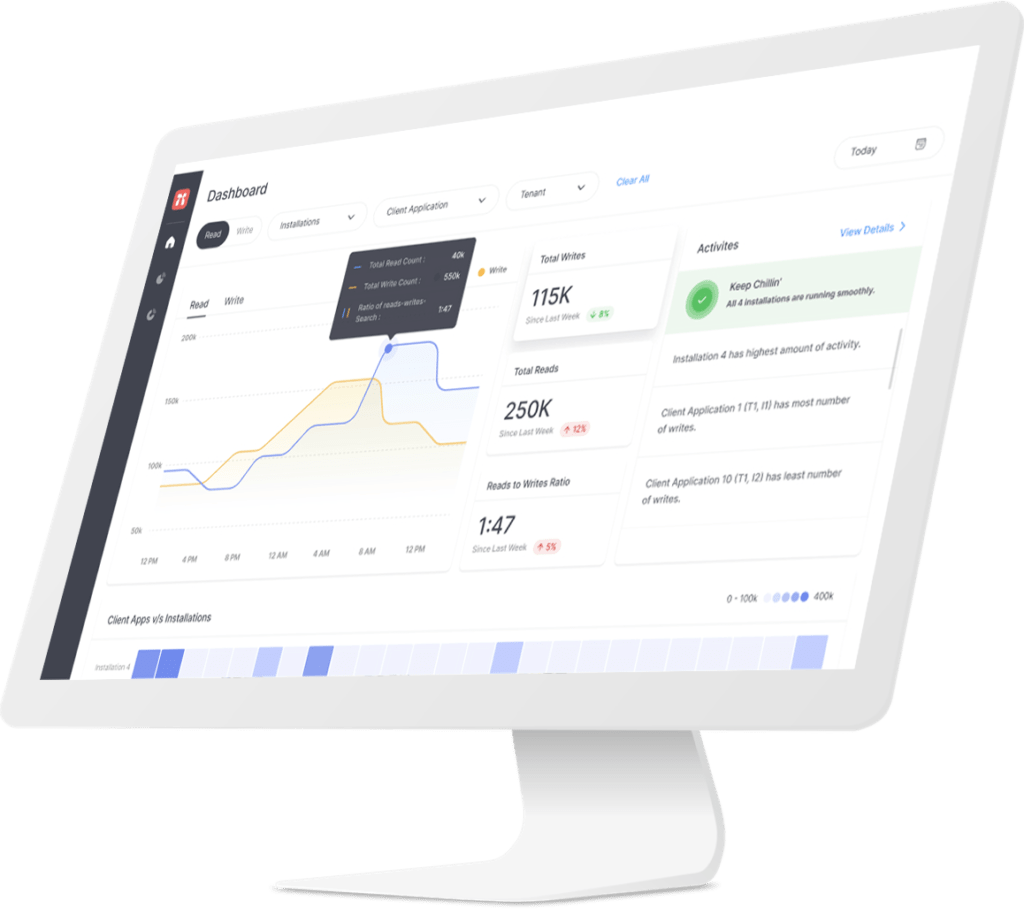
Portal26 Studio
Configure and manage Portal26 modules and services. View logs, dashboards, and reports.
Why Should I Add Portal26 To My Data Security Toolbox?
Portal26 encryption meets with the most stringent data protection standards in all major regulations and frameworks.
Portal26 releases data in all nine privacy preserving formats so it can be individually configured for downstream systems and users.
Compared to traditional, extortionate tokenization solutions, Portal26 secures as much data as needed while retaining usability.
The Portal26 plugin can be fully operationalized within a half a day, whilst the Proxy takes a few days.
In any attack scenario, Portal26 provides visibility into any data that was observed, accessed, or exfiltrated.