CISO Guide to DSPM: 4 components, 3 flavors, but there’s 1 the CISO favors
Did you notice the little rhyme in the title? This blog is dedicated to the newest buzzword in data security – DSPM. In this guide, I will cover the different ways in which I have encountered DSPM and also share how we define this at Portal26.
As always, these educational blogs are intended to provide simple frameworks and overviews of these topics without too much jargon.
What is DSPM?
Data Security Posture Management, as the term implies, seeks to assist enterprises in reducing data compromises by actively monitoring the security and usage of their data assets. Practically speaking, this is a large and serious goal, and given the sprawl of data and applications across the typical enterprise, this is not easily achieved. Also, as in the case of most other domains, different categories of vendors tend to define this term in different ways, and much of the time, these definitions align with their specific offerings in the area.
Portal26 offers strong and comprehensive data security features that speak very elegantly to a portion of the DSPM challenge. I will highlight these in this blog where appropriate but also acknowledge that there are currently more parts to the DSPM problem than offered by any single vendor, regardless of their claims.
Before we look at the flavors of DSPM that we have encountered in conversing with CISOs and vendors, let us look at DSPM and the four components of DSPM in more detail.

What does DSPM mean?
DSPM stands for Data Security Posture Management and it is considered the hottest new category of solutions in the data security space. Terms such as DSPM are typically coined by industry analysts to help customers sort through hundreds of vendors and match them with an equally large number of enterprise use cases.
4 Components of DSPM
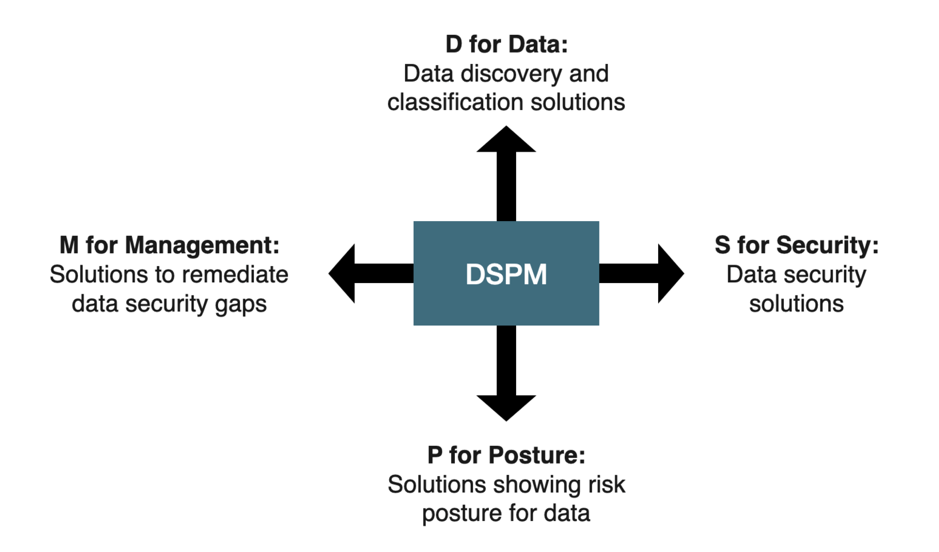
D for Data: Data discovery and classification solutions
The D in DSPM speaks to data and it is no surprise that the large number of solution providers that offer data discovery and classification solutions are staking a claim to the DSPM space.
A few points that CISOs have brought forward in conversations:
- Knowing what data we have is absolutely the first step so we see the value in that, but these solutions have existed for a long time. It does not seem right that this should be presented as a complete DSPM solution. What about the rest of it?
- Some providers are restricting their definitions of DSPM to the cloud. How is this complete? A very large number of enterprises have hybrid environments, with a significant amount of data still residing on-prem. Should the D in data refer to both cloud and on-prem?
- The enterprise data landscape is very large and very diverse. We need further categorization within the D to speak to what type of data is addressed by the particular DSPM solution. Is it based on broad strokes such as structured and unstructured data? Is it based on a repository or platform? Is it based on particular clouds? Is it vertical or domain-specific?
S for Security: Data security solutions
The S is DSPM stands for security and it certainly makes sense to have data security solutions be part of the DSPM story. However, there are a very large number of solutions and they collectively offer at least ten types of security controls – so from a CISO standpoint, all DSPM solutions that form the basis of their claim in data security are definitely not created equal.
Here are some of the questions that have come up from CISOs when looking at the data security aspects of DSPM:
- What types of data security controls are included in the DSPM offering? Does the solution bring together more than one control category? (Data security controls include functionality such as traditional encryption, format-preserving encryption, various types of tokenization, data masking, advanced encryption functionality such as encryption-in-use, hashing, anonymization, and so on.)
- Do the data security control included in the DSPM platform apply equally well to structured and unstructured data? What about various platforms, databases, repositories, and applications? Are they restricted to cloud data, or do they cover hybrid environments as well?
- How granular are the data security controls included in the DSPM platform? If the application of controls is not sufficiently granular, the level of security offered is not as strong. This is because when controls are applied at a coarse level, granular data usage requirements mandate exposing larger volumes of data than necessary to fulfill the business use case.
- The most interesting question we have heard on this aspect of DSPM is whether the platform joins the dots between the D and the S i.e. is the platform able to discover and classify data and at the same time expose the level of security that has been applied to it? Having both makes DSPM dashboard different from only D or only S solutions.
The D and S together appear to be the minimum bar for inclusion into DSPM. A solution claiming DSPM should enable visibility to both the data as well as the security that has been applied to it. The rest of the acronyms, P and M, add to the baseline.
The next two are the more nuanced and interesting aspects of DSPM.
P for Posture: Solutions showing risk posture for data
The P in DSPM stands for Posture, and here is where things start to get interesting. With CSPM (Cloud Security Posture Management) having become a known category, there is a bit of overlap and a lot of confusion between CSPM and DSPM.
CSPM is an overarching category covering the security posture of all cloud resources, including but not limited to data. DSPM is a data-specific concept and, ideally, should go beyond cloud data. One could think of CSPM as including lightweight DSPM, but it would not be right for CSPM solutions to claim the DSPM category without increased focus on data-specific discovery as well as security enforcement.
Now that we are done with clarifying DSPM versus CSPM – let us look at what the P brings to DSPM beyond what the D and S already brought.
The word posture implies an evaluation of the quality of data security. In other words, a solution that discovers data and exposes the security controls applied to it is just a visibility solution. It goes from a visibility-based solution to a posture-based solution if and when it can provide an assessment of how secure the organization’s data is. Further, an assessment of security, by definition, must be against some sort of framework or baseline.
There are a number of options for this, such as:
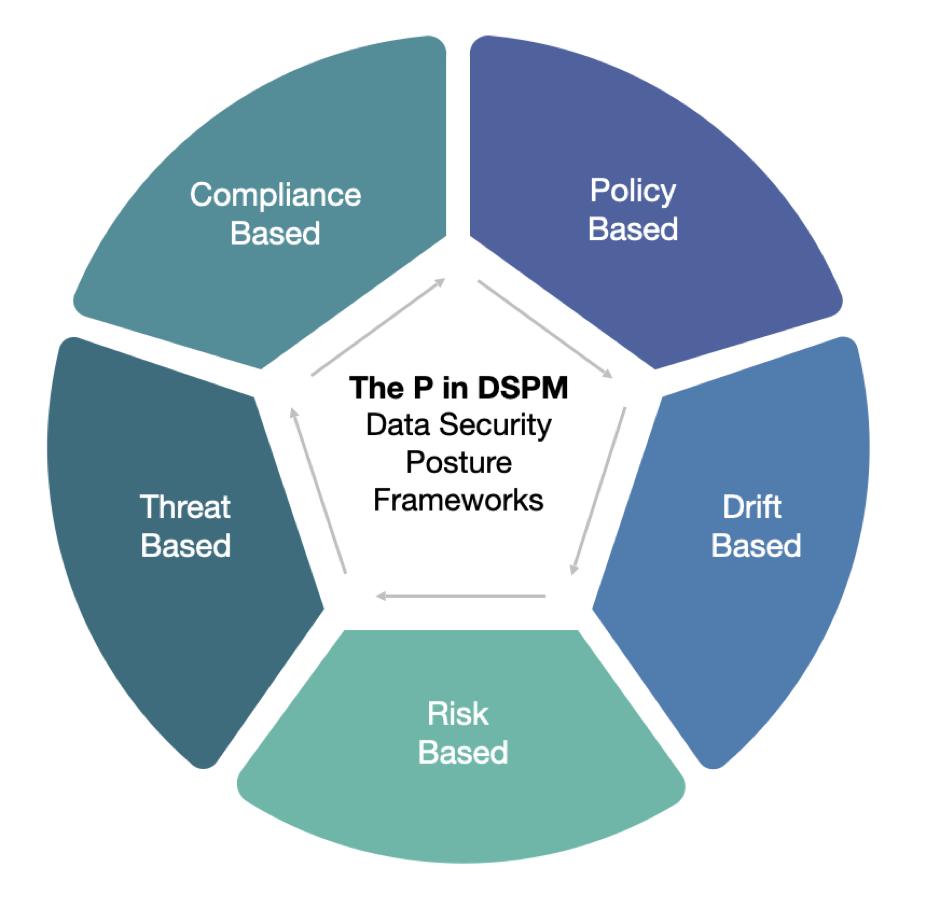
- Compliance-based frameworks – evaluating data security posture against a compliance-based framework would help an enterprise look at gaps in their data security controls in the context of specific regulations or legal mandates. A compliance-based DSPM dashboard would be very useful for compliance officers, privacy officers, DPOs, and also for the CISO office.
- Policy-based frameworks– evaluating data security posture against a set of granular policies can also be very effective in understanding an organization’s data security posture. Policies can be set based on external mandates as well as internal guidelines. Once set, DSPM dashboards can provide a useful tool for organizations to understand where they stand relative to the requirements
- Drift-based frameworks– evaluating data security against a set of configurations that were previously approved is another popular way of looking at data security posture. Obviously, this can be a combination of compliance and policy since approved configurations can be guided by a number of reasons. Drift-based dashboards are interesting as they provide a much more flexible approach to data security than either compliance or policy-based approaches
- Threat-based frameworks– evaluating data security against a set of current threats is a very interesting and also the most advanced way to look at the data security posture of an enterprise. Using a threat-based framework to evaluate your data security posture gives you a very good idea of gaps and actions that need to be taken to address those gaps. Further, and most importantly, threat-based frameworks provide a lot of useful information that can feed into a data risk model, which is the ultimate powerful way to evaluate data security (or another type of security, for that matter) posture.
- Risk-based frameworks– evaluating data security against an organization’s appetite for data risk is the ultimate goal for any risk posture evaluation and this is also true for DSPM. In order to assess the data risk and compare it across organizations or over time, the DSPM solution must utilize a standardized risk framework. A risk-based framework generally incorporates various types of risk, including compliance risk and threat-based risks, as described above.
As in other types of DSPM claims, CISOs are asking pertinent questions about the P in DSPM:
- How does the DSPM solution differ from traditional data discovery and data security tools? What does it offer in addition?
- How well does the DSPM tool capture security posture? Does it break down posture with respect to required regulatory compliance, internal policies, configuration drift, threats and vulnerabilities, and overall risk?
- Are some DSPM tools more comprehensive than others in their capturing of security posture? Does it provide us with a red/ green assessment of where we stand? Is it actionable?
- Is the coverage of visibility, security, and posture consistent across different types of data as well as various types of platforms, repositories, and apps? If not, is the coverage that is provided consistent with the organization’s priorities?
M for Management: Solutions that provide the management i.e. improvement or remediation of data security posture
The M in DSPM stands for Management and is the most easily overlooked. However, it is one of the most important parts of DSPM because it is what sets the old data discovery, data security, and data mapping tools apart from true DSPM. Management of anything, including the management of data security posture, by definition, involves some sort of iteration where an aspect of poor posture i.e. risk can be remedied by taking action in the DSPM platform (or from the DSPM platform via integration) – and once remedied, the outcomes are reflected in the DSPM dashboard as an improvement in posture.
A key attribute to look for when evaluating the M is DSPM is automation. If it is indeed possible to add as an element of automation toward improving data security posture in response to risk-based triggers, then we would see a DSPM platform in its truest sense.
CISO questions we have encountered with respect to the management of security posture are the following:
- Can DSPM solutions measure the improvement or decline of data security posture over time?
- Can DSPM solutions leverage existing security investments to implement the closed loop on posture management?
- Can posture management exist without data discovery and classification, and would that still fall within the DSPM umbrella?
The last question above is a great segue into the 3 flavors of DSPM we are seeing in the market today.
3 Flavors of DSPM in the market today
A quick summary of everything that is included in DSPM for a truly complete solution:
- Data discovery
- Data classification
- Data security controls visibility
- Gap assessment against compliance requirements
- Gap assessment against data security policies
- Drift from accepted posture/data security configurations
- Gap assessment against current threats and vulnerabilities
- Gap against risk framework
- Data security controls implementation to close the above gaps, preferably automated
- Visibility into posture improvement
A quick look at the list above, and we can see why there is not a single solution that addresses all of DSPM in the strict sense. However, there are several flavors of DSPM that do exist in the market today.
3 common DSPM flavors are:
DSPM Lite
When CSPM vendors add some coverage for cloud databases (DBs) and repositories, what you get is DSPM Lite. This is not the flavor of DSPM that CISOs are finding interesting based on our conversations thus far since it is viewed as more of a marketing stunt than anything real.
D+SPM via integration
When data discovery vendors include structured and unstructured DBs as well as add a dashboard for data maps you get a solid take on one-half of DSPM. When this is combined with a DSP (data security platform) via integration, you get the other half as well, and together you have a very healthy DSPM solution. This version of a DSPM offering brings the best of data security and integrates it with the best of data protection.
(Disclosure: Portal26 offers a solution along with a partner in this area. To schedule a briefing please book a demo over on our demo page)
DSPM without discovery
When a data security platform vendor includes comprehensive data security controls i.e. all ten categories of controls, and has a mechanism to deploy these across the breadth and variety of data platforms, repositories and applications – and can also dashboard granular data security, movement in security posture over time, application and evolution of data security policies as well as application of data security controls in response to compliance or policy requirements, what you get is DSPM without data discovery.
(Disclosure: Portal26 offers this solution. To schedule a briefing please book a demo with our team by visiting our demo page).
The gap between this and a full DSPM is data discovery and these platforms take one of two approaches to bridge this gap:
- Secure everything – thus removing the need to scan and classify before applying security. Secure everything sounds like a bold sweeping concept but it is quite practical in the world of unstructured data. Scanning documents for sensitive data and then targeting the data security solution towards isolated data items can be replaced with securing entire documents. Advanced data security options like encryption-in-use can facilitate data manipulation without losing security.
- Integrate with a data discovery solution – thus creating the category described above in D+SPM via integration
The DSPM flavor that CISOs favor
With all these variations in the market, we checked in with CISOs to see what their thoughts were in this area.
With the threat landscape evolving to a point where we are basically losing the data security fight, 2023 is seeing CISOs that want to move decisively towards actually securing their data and not just be satisfied with visibility-based dashboards.
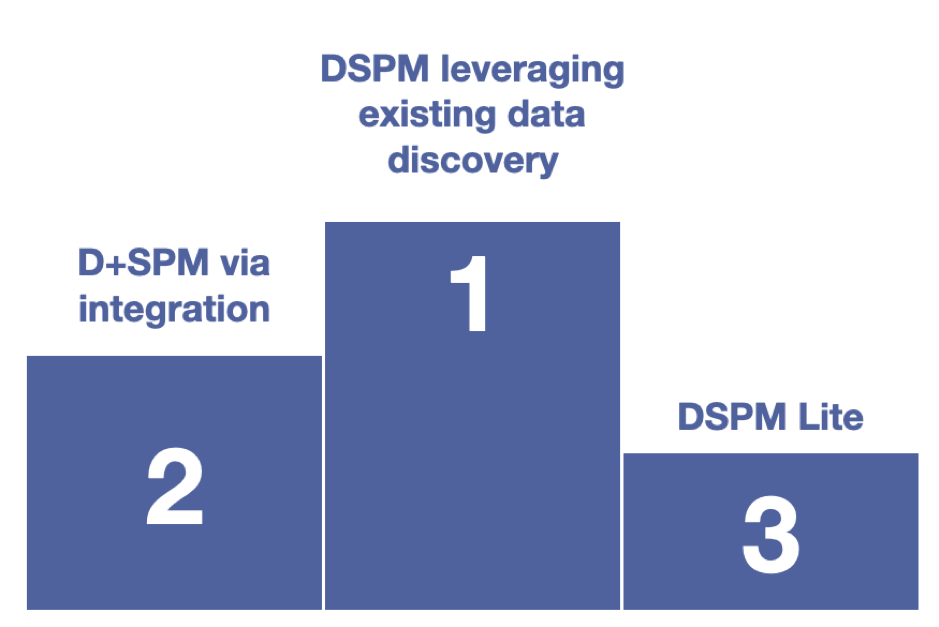
So, in the end, if budgets are limited or choices have to be made, the order of preference for DSPM is as follows:
First – True protection (DSPM focused on strong data security that leverages existing discovery investments)
Second – Discovery + Protection (DSPM via integration or leveraging existing data security investments)
Third – CSPM with a focus on data (DSPM Lite)
Conclusion: DSPM is a grand idea
If you can have it all, go for discovery, classification, all ten categories of data security controls, risk-based posture management, and automated remediation. If you can’t have it all, opt for a DSPM with a strong focus on actual data security because when attackers strike, visibility alone will not help you.
Portal26 provides the industry’s richest and most advanced data security platform
Portal26 provides coverage for structured and unstructured data across all types of databases, object stores, search platforms and repositories.
Portal26 provides all ten data security and privacy control categories in a single engine ranging from traditional encryption and tokenization to advanced searchable encryption and encryption-in-use. Rich dashboards provide data security posture information and granular visibility into security posture during attacks as well as evidence of security for auditors and regulators.