CISO Guide: 3 Strategies to Maximize Cybersecurity Budgets for Data Security
This edition of Portal26’s Data Security Blog is dedicated to optimizing cybersecurity budgets as they relate to securing enterprise data . With the economic forecast being gloomy and waves of budget cuts as well as layoffs, it has become more challenging than ever before for CISOs to afford all the security controls that their organizations need in the present threat climate.
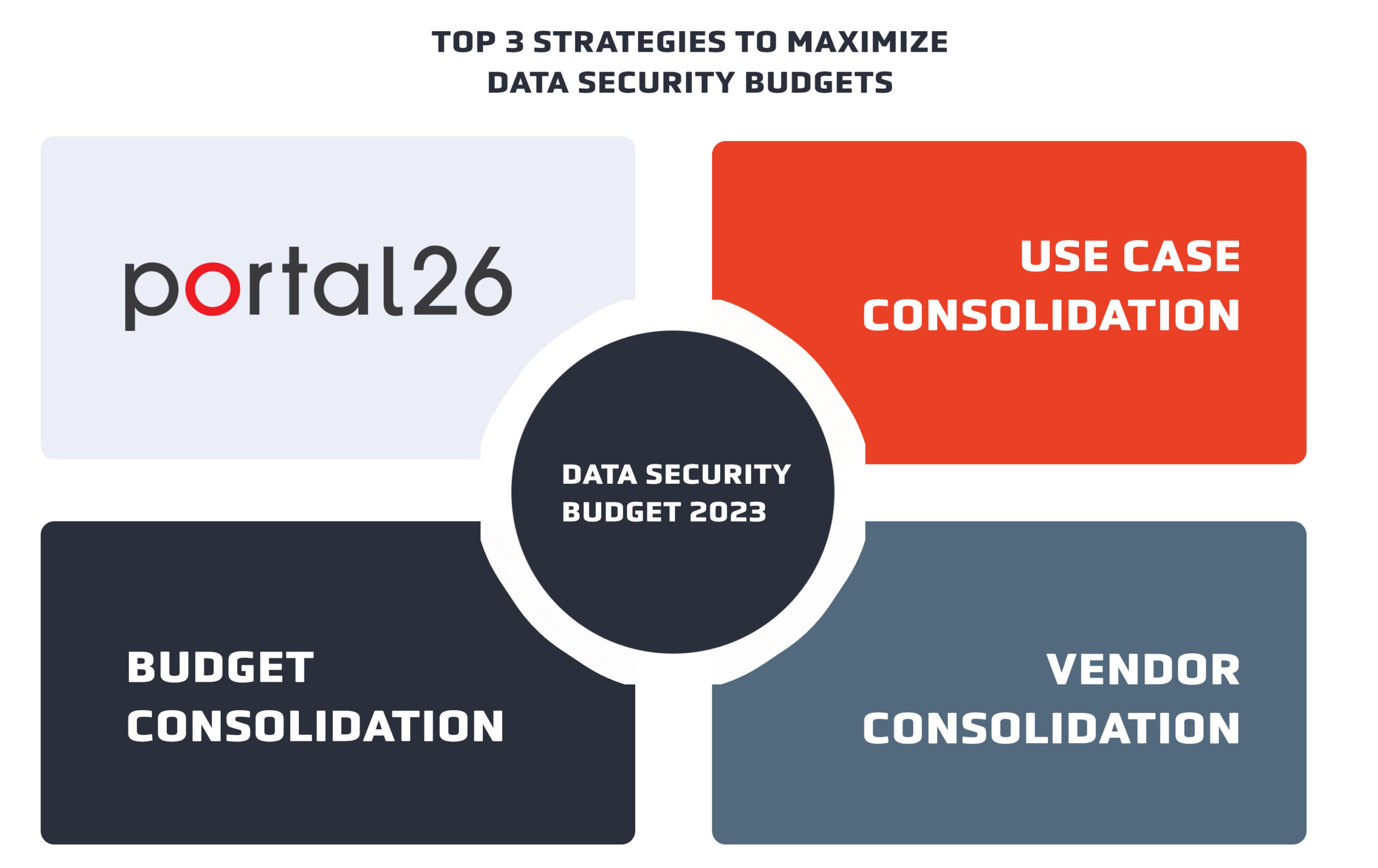
As always let’s get the Portal26 angle clarified up front. A big part of the CISO wisdom on the topic of cybersecurity budgets for data security is about consolidation – consolidation across use cases, consolidation across vendors, and consolidation across budgets.
These three also happen to be basic principles on which Portal26 was created and so there is a lot of overlap between the budget optimization story and Portal26’s value proposition.
Also, for the practical reality of what needs to be accomplished inside organizations against available cybersecurity budgets for 2023, there are not too many Portal26 like options out there – and our in-depth understanding of our own platform allows me to provide real world examples where applicable.
So, you will see these throughout this edition of Portal26’s Data Security Blog.
Data Security Budgets for 2023
According to Portal26’s 2023 Cyber Security Predictions Survey, data security remains a top priority for enterprises. If you combine generally stated data security projects (greater than 30% of enterprises) and projects aiming to secure data against ransomware and extortion (a bit less than 30%), we are looking at over 60% of enterprises who have recognized data security as a top 2023 priority in some form or another.
The economic climate going into 2023 is tough and so for this year all purchases will need to be examined through the lens of economic efficiency. The question for CISOs this year is: How can you fulfill your objective of strong data security without straining your budget?
Here are recommendations based on Portal26’s interactions with CISOs as well as what we are seeing in projects in the field.
Consolidation is the Name of the Game
What is vendor consolidation? Based on what we are seeing in the market, CISOs who are presenting consolidation-based strategies to their executive leadership and board are seeing more success with their data cybersecurity budgets than those that are sticking to one off projects/priorities in their proposals.
Here are the Top 3 data security consolidation strategies that are winning/have won budgets going into 2023:
- Consolidation across use cases
- Vendor consolidation
- Consolidation across departmental budgets

Consolidation across Use Cases
Currently all major analyst and research houses are pushing the idea of use case consolidation in data security. From the new, bright, and shiny DSPM, DDR (Data detection and response), the prior acronym DSP (data security platform) and one Gartner used for a while – Broad Spectrum Data Security Platform, it is clear that many industry pundits are pushing a use case consolidation story.
This means that CISOs should consider favoring platforms that address more than one internal initiative. At Portal26, as we have met with CISOs across verticals, our most successful conversations have been ones where CISOs have brought multiple initiatives into a single investment decision.
When presented with a multi-use case investment CISOs tend to ask the following two questions. Having good answers to these boosts their argument for budget:
- Are all presented use cases equally well served? A good answer here prevents CISOs from dropping back to the very expensive best-of-breed arguments from prior years.
- Do multi-use case solutions suffer from performance issues? High latency for enterprise grade use cases can be a deal killer.
Portal26 for multi-use case investments
Portal26 was built with the idea of collapsing many use cases into a single solution, while maintaining high-performance for high-throughput, petabyte scale use cases.
The Portal26 solution offers a converged platform for the following use cases/technologies/security controls.
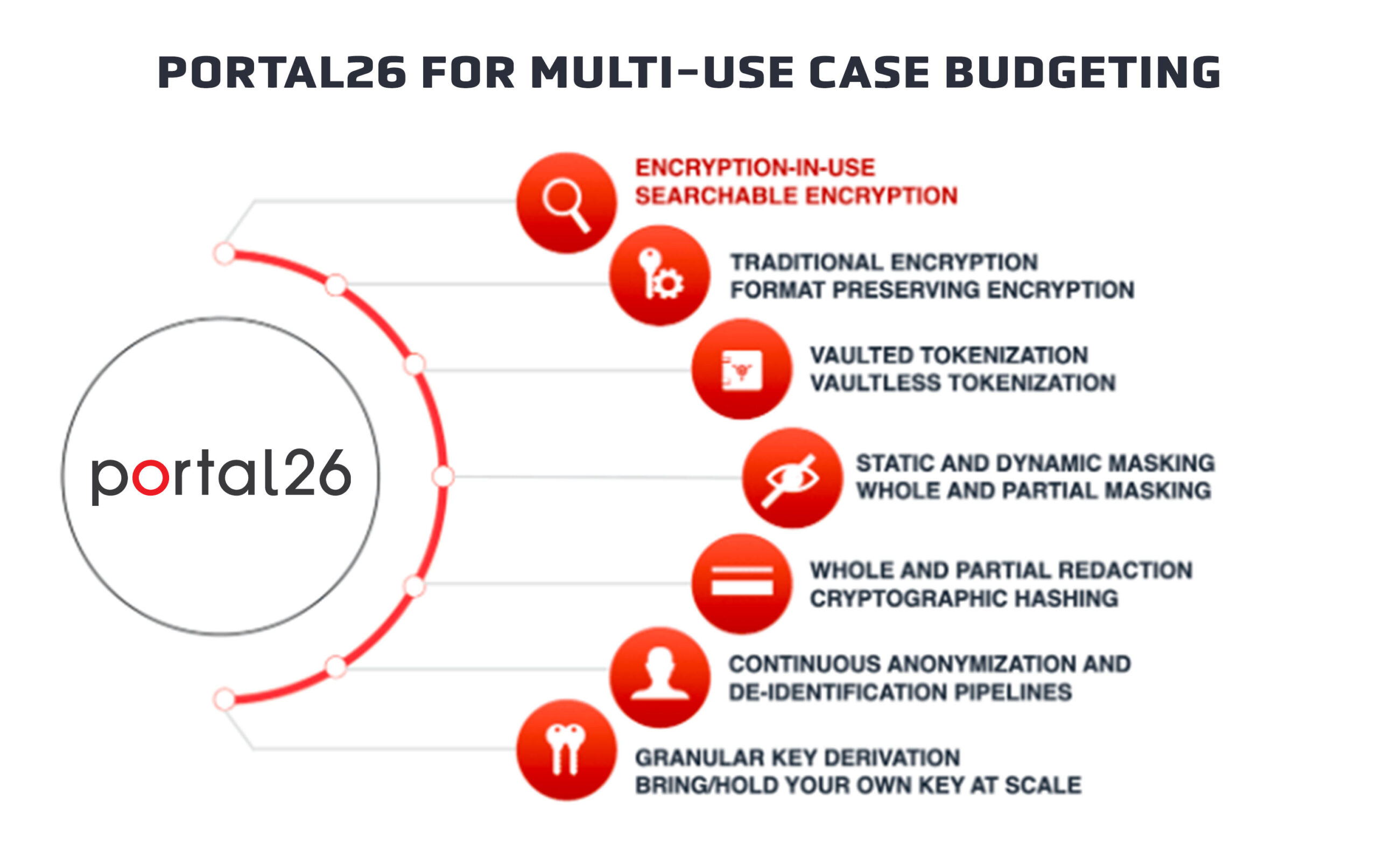
Since different people make their lists differently, I am presenting a “messy” list. This includes pure controls, application of controls, and true use cases all mixed together:
- Encryption-in-use/ Searchable Encryption
- Traditional Encryption
- Format Preserving Encryption (FPE)
- Vaulted and Vaultless Tokenization
- Static and Dynamic Data Masking
- Whole and Partial Redaction
- Anonymization/De-identification using multiple privacy preserving formats
- Cryptographic Hashing
- Field Level Key Derivation
- Bring/Hold Your Own Key (BYOK/HYOK)
Applications or Use Cases for the above controls are all supported within a single Portal26 solution, representing one of the industry’s best examples of use case consolidation and strong budget support.
Examples of applications and use cases are below:
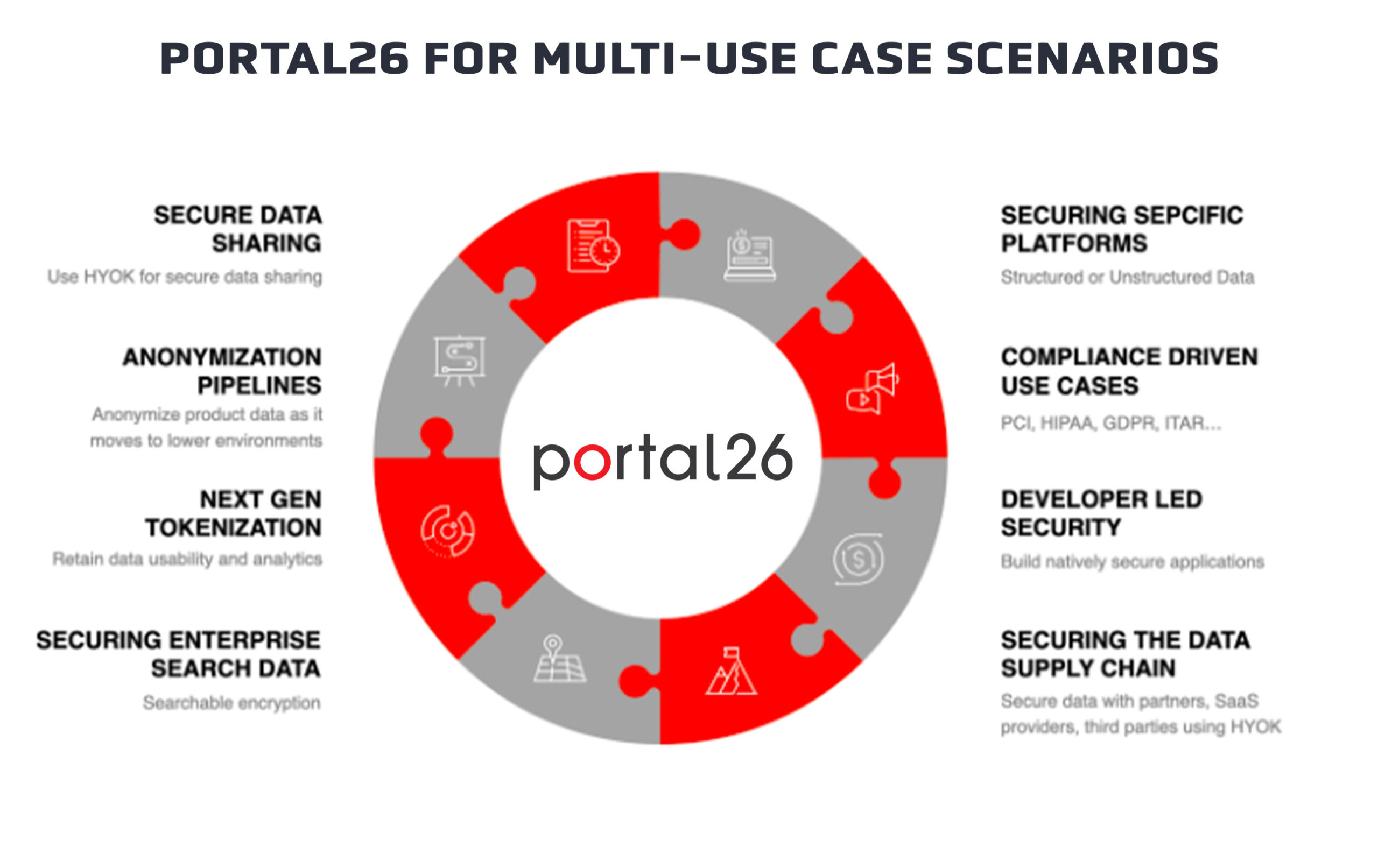
- Securing structured and unstructured data in specific platforms, databases, data lakes, repositories, and applications
- Making specific applications and datastores compliant with regulations like PCI, GDPR, etc.
- Developing applications that are natively secure against data compromise i.e. developer led security
- Securing data against supply chain attacks
- Secure data sharing and collaboration
- Dev to test data anonymization
- AI/ML data privacy
- SaaS data security and compliance
- Securing enterprise search use cases
If you read the above list carefully, you will see each of these has the potential to drive its own budget and ROI.
For Portal26, having the ability to offer it all in the one platform, allows us to help CISOs make a very strong case for investment.
Other benefits include:
- Easy budget justification
- Additional use cases without additional deployments
- Additional use cases leverage the same platform features and back-end integrations
- Additional use cases leverage the same policies and drive consistency
- Lower cost per use case
- Single management console and reporting across use cases
Security Vendor Consolidation
Vendor consolidation is another big focus for CISOs going into 2023. These days, the more modern data security platforms are able to replace many point solutions and present excellent cost saving opportunities.
Data Security Platforms Available
Today there are three types of data security platforms in the market:
I. Single use case, single platform offerings
Many vendors, traditional and newly funded, do not offer anything beyond a single use case for a single platform. Some believe staying hyper focused is the right approach but the current market appears to only reward this if that hyper focused use case is a top3 strategic initiative. If this happens to not be the case, it is tough for vendors to make it. Examples of these would be data masking solutions for particular platforms, or encryption solutions for particular file shares, or log cleansing solutions for particular SIEMs and so on. I’d like to stay away from being too specific so that I do not paint any vendor in a bad light. In any event, single use case solutions present a challenge for the vendor as well as the CISO on the other end of the purchase decision.
Vendor challenges include:
- Inability to justify more than minimal cost
- Inability to demonstrate enterprise-wide applicability
- Inability to justify integration expenses
- Inability to truly secure data against real world attacks since these present low data coverage relative to the extent of data sprawl faced by the enterprise
- Inability to bring in sufficient revenue to maintain operations or to secure venture financing, thus creating a customer confidence issue
- For the more established single use case vendors, they are seeing a significant decline as multi-use case vendors eat into their market share
CISO challenges include:
- Inability to justify additional budget for a new investment or a rip-and-replace since there are limited additional benefits. The only scenario where this would still work is if the new solution is dramatically less expensive.
- Becomes another point solution to manage
- Cannot benefit from broader visibility
- Harder to justify investment since vendor presents a higher risk profile
- Adds to the integration load since each point solution needs to be integrated into the broader architecture
- Harder to get peer and executive buy in for budgeting
- Individual use cases do not get exec or board level visibility
II. Single Use Case, Multiple Platform Offerings
These solutions take a single use case and make it work across multiple platforms. These are a little easier to justify for CISOs especially if there are multiple platforms that have significant market share for that particular use case. This type of offering has a lot of players and has attracted a good amount of investment.
Vendor challenges include:
- Different platforms tend to speak to different customers but within a single customer this looks a lot like a single use case single platform offering and faces all the same limitations.
- Within a single customer’s context they still face the Inability to justify more than minimal cost
- Within a single customer’s context they still face the inability to demonstrate enterprise-wide applicability
- Within a single customer’s context they still face the Inability to justify integration expenses
- Within a single customer’s context they still face the Inability to truly secure data against real world attacks since these present low data coverage relative to the extent of data sprawl faced by the enterprise
CISO challenges include:
CISO challenges include all the same challenges as single use case single platform if a given CISO generally uses these on a single platform:
- Inability to justify additional budget for a new investment or a rip-and-replace since there are limited additional benefits. The only scenario where this would still work is if the new solution is dramatically less expensive.
- Becomes another point solution to manage
- Harder to justify investment since vendor presents a higher risk profile
- Adds to the integration load since each point solution needs to be integrated into the broader architecture
- Harder to get peer and executive buy in for budgeting
- Individual use cases do not get exec or board level visibility
III. Multi-use case multi-platform offerings
As long as these solutions are built to support enterprise grade use cases without high performance overheads, these solutions are best suited to meet the enormous data security needs while satisfying todays budgetary challenges.
Vendor advantages include:
- Easy justification for budget
- The ROI story gets better and better with each use case
- The deployment and integration story also gets better with additional use cases and platforms
- Multiple platforms and use cases in a single management console and policy is exciting and visible
- Executive and board level visibility and support
CISO advantages include:
- Easy to justify budget
- Presents as a strategic investment
- Single investment pays off dividends for many years
- Cost and resource efficient
Multi-use case multi-platform solutions are easiest to justify and also result in vendor consolidation. Vendor consolidation further adds to the advantages in the following way:
- Reduction in integration
- Reduction in vendor risk
- Reduction in cost
- Ease of administration and reporting
Portal26 is the industry’s richest multi-use case multi-platform data security solution
Portal26 provides all security and privacy enforcement controls in a single solution and delivers it via six modules to all types of databases, repositories, applications and to developers across the enterprise. The level of flexibility, composability, and coverage offered by Portal26 is unprecedented and so Portal26 drives extremely strong, well-budgeted, and highly visible data security initiatives.
Whether you are looking for cutting edge encryption-in-use to shut down those ransomware extortion threats or looking to run a strong enterprise-wide privacy enforcement initiative, Portal26 has in our one engine, every control you can find in every other solution out there.
Consolidation across departmental budgets
The third and final strategy we are seeing to support data security budgets in 2023, is consolidation across departmental budgets. This refers to the pooling of resources that we are seeing take place when multi-use case multi-platform solutions gain visibility and create excitement inside the enterprise.
For me, this was something unexpected but when we saw it play out, it made a ton of sense. We have seen this in a few cases in organizations with the following attributes:
- Data security is a true strategic priority
- Data is viewed as a critical asset
- Multiple executive positions have significant data related responsibilities e.g. CISO, CDO, Chief Privacy Officer, CPO
- Prior strategic initiatives have already forged a collaborative path between departments. Examples are: CDO and CISO are already collaborating on ML initiatives, CISO and Chief Privacy Officer are already collaborating on Dev to Test data anonymization pipelines etc.
Portal26’s Data Security Platform is the broadest offering in the market and has the functionality needed for many enterprise wide, multi-platform, multi-cloud, and hybrid use cases. We are seeing 2023 data security budgets for solutions like Portal26 garner support from multiple stakeholders, especially in the context of initiatives that already go across departments.
Conclusion
Consolidation is going to be the leading, if not the only way for CISOs to support all the cybersecurity initiatives they will need to stand up to attackers this year. Use case and vendor consolidation is the name of the game for CISOs in 2023!
Those that can also pool in cybersecurity budgets with their CDO and CPO counterparts can get even more done this year!
To learn more about Portal26 please explore our products or schedule a demo today!