Portal26 Fileshare Proxy
Securing User’s Unstructured Data From Ransomware, Data Breaches, And Insider Attacks
Are you worried you could be hit with a ransomware attack and confront the compromise of your users’ data? Do you find it challenging to enforce file security and data privacy controls without getting in the way of business workflows? Portal26 offers the industry’s most advanced data protection software that ensures bad actors or malicious insiders with privilege can still not exfiltrate valuable files in unencrypted form.

Enterprises users’ unstructured data is typically scattered across a variety of file storage and sharing platforms, and can be in on-prem, cloud, or hybrid environments. Unfortunately internal and external bad actors routinely exploit trusted access channels to bypass traditional controls such as access control and encryption-at-rest to exfiltrate valuable data.
One of the most common ransomware scenarios is where attackers get inside the firewall, move laterally across the organization, and gain privileged access to an unstructured data repository from which they exfiltrate as much data as possible. Once in the repository, their credentials give them access to unencrypted files and with these in hand they are able to mount a vicious extortion campaign. Enterprises who fall victim to clear text data exfiltration end up giving in to ransom demands even if they have the ability to recover systems from backup on their own.
Aside from security concerns stated above, enterprises are also subject to a host of data privacy regulations which require them to have a firm handle on personal data in both structured as well as unstructured data repositories. For all these reasons it is important for organizations to invest in a modern data protection software solution that secures unstructured data against ransomware attacks, data breaches and insider threats, while still making it available for business use cases and without a heavy performance overhead.
“Protecting sensitive data while it is being used is the next frontier of data protection. It is really important for enterprises to have a default state for their data that is private and secure at all times, including when it is actively being used”
– Vishal Gupta
Global CTO & CIO, SVP Connected Technology at Lexmark
Portal26 Fileshare Security Key Capabilities
Portal26 provides enterprises with a unique and market leading data security platform that provides strong data security for unstructured data on fileshares while remaining completely transparent to the user themselves. Unlike other solutions that rely on agents on user endpoints, Portal26 focuses on securing against the largest risk vectors i.e. privileged access to the fileshares themselves and large scale exfiltration. Portal26 does not require agents on end user machines or devices.
The following are Key Capabilities for this Portal26 Data Protection software module:

Seamless Encryption

Eliminate Attacker Leverage

No Unauthorized Browsing

Encryption Keys, BYOK/HYOK
Supports Multiple Fileshares

Audit, Compliance, and Post-Attack Support
Portal26 Fileshare Security Architecture
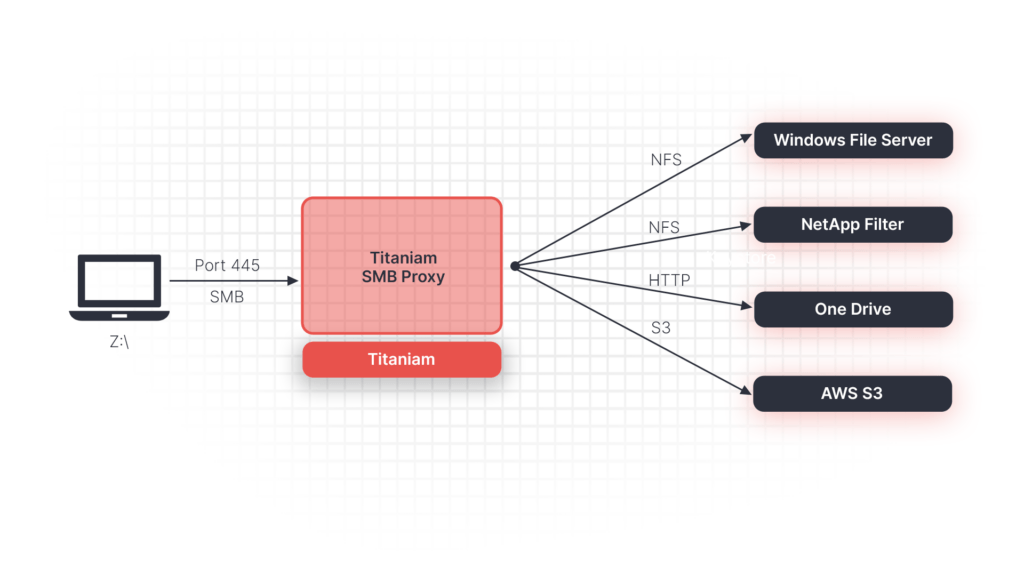
- Portal26 is deployed on the fileshare itself via agent or in front of it via proxy depending on the underlying file sharing platform and operating system requirements. In the case of file servers that allow agents, Portal26 agents are deployed on each file server. In the case where this is not permitted, Portal26 can be deployed via proxy.
- In either case files being written to the fileshare would be intercepted by Portal26 and encrypted on the way in. Portal26 utilizes strong NIST FIPS 140-2 certified encryption to provide this functionality.
- In addition, Portal26 brings with it rich BYOK (bring your own key), HYOK (hold your own key) and key control functionality. This enables different data owners I.e. users, groups, departments, entities, etc. to ensure that their data remains strongly segmented and private even if it resides on the same file server or directory.
- Encryption key based segmentation is also extremely relevant for regulatory compliance, data privacy, data residency, least privilege, and other compliance requirements. Key location and key management can provide companies with a strong and efficient security control with a broad span of enforcement.
- When Portal26 encrypts files the encryption includes the data itself as well as names of files and folders as well. This makes it challenging for bad actors to traverse these repositories to pick and choose the data they want to take.
Why Should I Add Portal26 To My Data Security Toolbox?
Portal26 encryption meets with the most stringent data protection standards in all major regulations and frameworks.
Portal26 releases data in all nine privacy preserving formats so it can be individually configured for downstream systems and users.
Compared to traditional, extortionate tokenization solutions, Portal26 secures as much data as needed while retaining usability.
The Portal26 plugin can be fully operationalized within a half a day, whilst the Proxy takes a few days.
In any attack scenario, Portal26 provides visibility into any data that was observed, accessed, or exfiltrated.
