CISO Guide: Cyber Resilience – How to Build a Data Security Program Resilient to Admin Compromise Post LastPass Breach
Executive Summary Up Front
- Admin compromises inflict maximum damage due to the extent of privilege associated with admin accounts
- Admin attacks can result in encrypted data loss (not a big problem as long as the encryption is strong and preferably NIST validated), clear text data loss (very big problem), and loss of encryption keys (enormous problem: Last Pass is an example)
- Modern Data Security Platforms (such as Portal26) enable data security programs that can be resilient to admin compromise
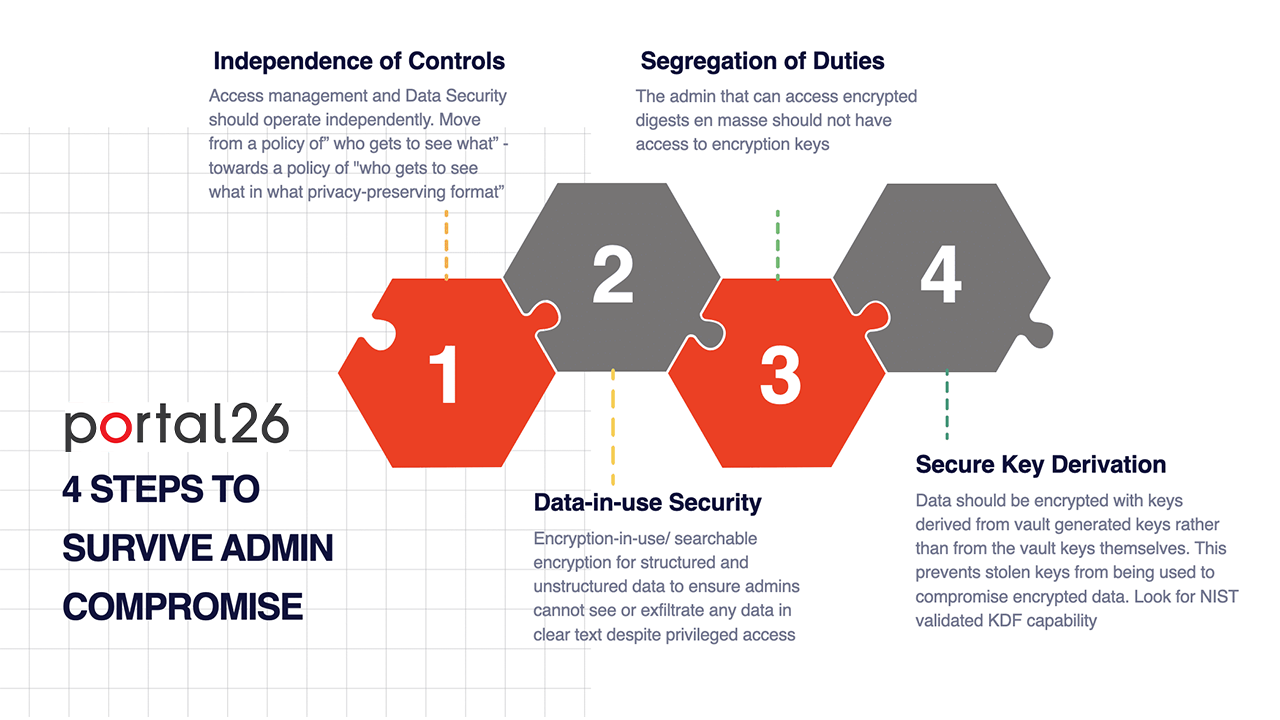
How Can You Create Cyber Resilience Against Admin Compromise? Key Attributes to Look For
- Independence of Controls: Independent controls for access management and data security (access alone does not guarantee clear text data).
- Data-in-Use Protection: Admins should never see clear text data even if logged in with highly privileged credentials (data-in-use protection/ encryption-in-use/searchable encryption).
- Segregation of Duties: The same admin should not be able to access encrypted digests as well as associated encryption keys,
- Not Using Vault Generated Keys Directly: Encryption keys from key vaults should never be used directly, rather encryption keys should be derived from vault generated keys in real-time to ensure that stolen vault generated keys do not automatically result in large scale data compromise. Look for NIST certified key derivation functions (KDFs)
LastPass Security Incident – The Background
This edition of the Portal26 Data Security Blog is focused on the very large elephant in corporate boardrooms and in CISO offices today: Admin Compromise. The LastPass data breach highlights the fragility of enterprise data security controls.
After deploying an extensive set of security controls by the book CISOs appear to be in a position to represent that the enterprise is well protected… but they know that if an administrator were to get compromised the entire security infrastructure will come down like a house of cards. The LastPass breach is this nightmare scenario playing out in real life.
While it is often true that victims of cyberattacks could have done a better job in protecting themselves, given that the deadliest breaches involve admin compromise, wouldn’t it be ideal if enterprise data security controls could be resilient against admin compromises?
Portal26 was purpose built to enable enterprises to withstand admin compromise
In our early days we would carefully explain to anybody that gave us their ear, that while user compromises are unfortunate and should be avoided, the biggest risks lie in compromised admins. These days we no longer have to explain. Day after day we are witness to organizations of all sizes losing large volumes of data to attackers who manage to impersonate administrators.
How To Build A Data Security Programme Resilient To Admin Related Data Risk
So here we will share what CISOs should look at while modeling admin compromise risk and how they can build a data security program that is more resilient to admin related data risks.
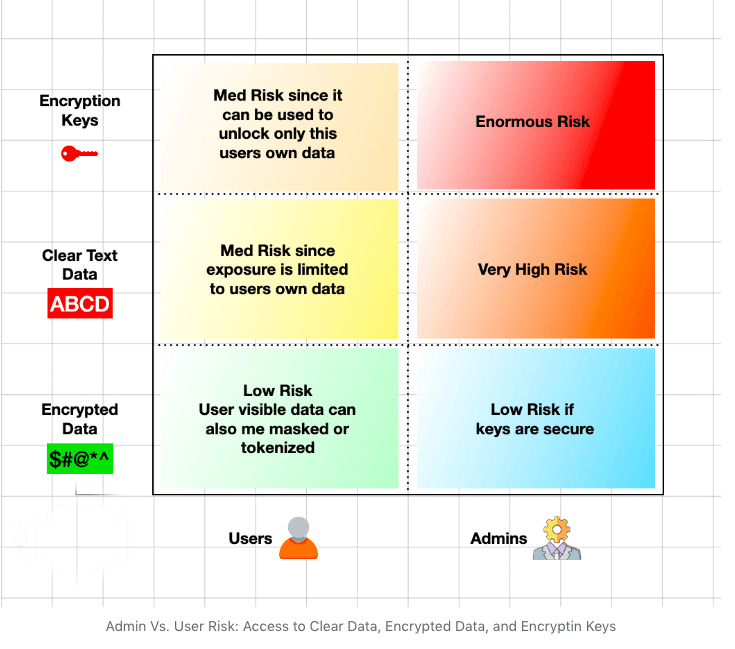
Users Vs. Admins: Risk matrix
Data is the most important asset in the enterprise. While it is important to keep data secure, it still needs to be made available to users. Given users do in fact need access to data, we can model what type of access they get and what it means as far as risk.
We can do the same for admins as well. Also, the Last Pass situation reminds us that it is not just data that we should be worrying about – we must be equally concerned with who has access to encryption keys and what the down side risk is if keys fall into the wrong hands.
Managing User Data Risk
User related risks can be managed in the following ways:
- Advanced access control measures such as granular access control, attribute based access control (ABAC), and policy based access control (PBAC)
- Combining access control with data security controls so that even if a user is permitted access to data it can be presented in privacy preserving formats to the extent that the user can still perform their business function – such as encrypted, format preserving encrypted, tokenized, masked, redacted, etc. If clear text is needed, it should be computed on the fly but not persisted (Portal26 offers this rich granular data security functionality across all modules and all supported repositories)
- Segmenting back end data using granular encryption keys to contain the blast radius in the event that a user gets compromised and attackers manage to move laterally across the organization. (Portal26 offers this functionality for all modules and all supported repositories). Portal26 can implement user or role specific encryption keys as well as file, object, field, and individual data element level keys.
Find Out More About Portal26 Data Security >
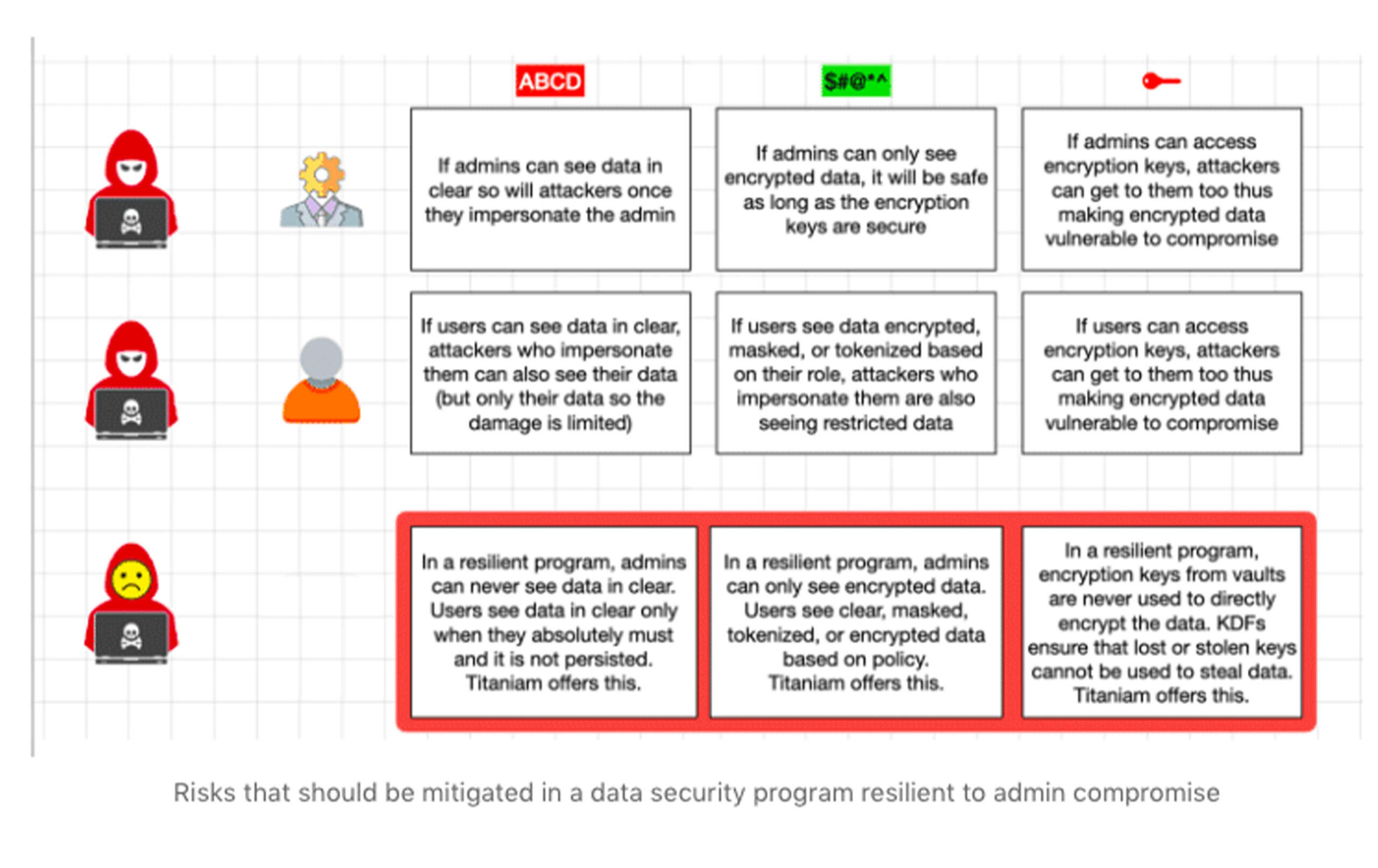
Managing Admin Data Risk
The framework here has to be very simple. If admins get compromised, whatever they have access to will get compromised as well. If there is a way to get to data and resources via admin credentials, it is only a matter of time before a sophisticated enough attacker finds their way to it.
One of the biggest mistakes organizations make with respect to admin privileges is that they protect them via access control alone. Without an inner data layer of defense, admin accounts represent the highest risk of data compromise.
Having a single layer of defense for the keys to the kingdom is not smart, and breaches such as LastPass provide a valuable lesson. MFA is necessary but as in the case of LastPass, it can be compromised.
Let’s have a quick look at exposure via the following table:
Security Best Practices For Administrator Accounts
Let us now go through each of the four recommended steps towards making your enterprise data security program resilient to admin compromises:
- Independence of Controls: Adding an admin focused data security control layer independent of access management can become the difference between walking out of a major breach unscathed or having a major event on your hands. In this context, additional data security controls would ensure that an admin would not be able to read databases, open files, or exfiltrate data simply by virtue of logging in as admin. In order to open any data specific resources, they would need specific rights to the specific files or tables. More importantly, even if they were granted access to data by virtue of an admin specific policy, their admin functions might be sufficiently served by having that data in aggregated, encrypted, tokenized or partially masked form. This level of granular policy ensures that there is no scenario in which admins gain large scale access to clear text data or the ability to exfiltrate large amounts of data from the organization. (Portal26 offers a granular fully independent set of data security controls that can be layered inside access controls to fulfill this approach.)
- Data-in-use protection: Adding encryption-in-use along with encryption-at-rest to a data repository ensures that any file system or database admin cannot see any data in clear text even if they have full privileges to the server or the database. Searchable encryption allows queries on encrypted data without decryption. If search and analytics are not a requirement, then other types of controls such as encryption, format-preserving encryption, tokenization and hashing can all ensure that server or db admins cannot access or exfiltrate data in clear. This basically means that if attackers impersonate admins and hijack privileges, they cannot get access to data either. Portal26 offers the industry’s most advanced high-performance encryption-in-use and searchable encryption solution that can be integrated into existing architectures to secure against large scale admin compromise.
- Segregation of Duties: As a general rule, encryption keys should never be stored along with the data. The system that is the keeper of the keys should not also be the system that is the keeper of the data. By the same logic, an admin that has access to encrypted digests should not also be the admin that has access to the encryption key vault. While nobody would openly disagree with this sentiment, we know from data on the ground that a very large number of organizations still have this type of concentration of risk in a handful of admins. Segregation of duties for encrypted data and encryption keys is not as easy to implement as it would appear on the surface. For this reason, the next and final step is the most important step in preventing admin related data compromise.
- Not Using Vault Generated Keys Directly: One of the most important controls that secures against admin compromise or key vault compromise is to never use vault key materials directly to encrypt data. NIST provides guidance on how to use KDFs (Key Derivation Functions) to strong keys that can then be used to encrypt the data. Portal26 offers a rich data security platform that includes modern ten data security and privacy controls where all encryption based controls (encryption-in-use, traditional encryption, format-preserving encryption) all use NIST validated KDFs to derive keys. Portal26 never uses vault keys directly and also never persists derived keys. In the event that both the encrypted digest as well as the encryption keys get compromised, attackers would still not be able to directly decrypt the data.
Solutions To Secure Data Against Administrator Compromise
Portal26 powers enterprise-wide data security programs that are resilient against admin compromises as well as compromised encryption keys
Portal26 offers the industry’s richest data security platform that provides a rich and independent data security framework that complements advanced access management.
Portal26 includes all ten data security and privacy controls in a single solution. This means that enterprises can have access to advanced encryption-in-use and searchable encryption as well as a comprehensive set of traditional controls such as traditional and format preserving encryption, vaulted and vaulted tokenization, static and dynamic data masking, anonymization, redaction, hashing, and key management, key derivation as well as bring/hold your own key.
Portal26 customers configure these controls to ensure that admins can not access data in clear text and hijacked admin credentials cannot be used to exfiltrate large volumes of data in clear text.
Further, Portal26 never uses vault keys directly. Granular keys for fields, objects, files etc. are all derived from master key materials on the fly but are never persisted. This ensures that admin or key based compromises do not have immediate catastrophic consequences.