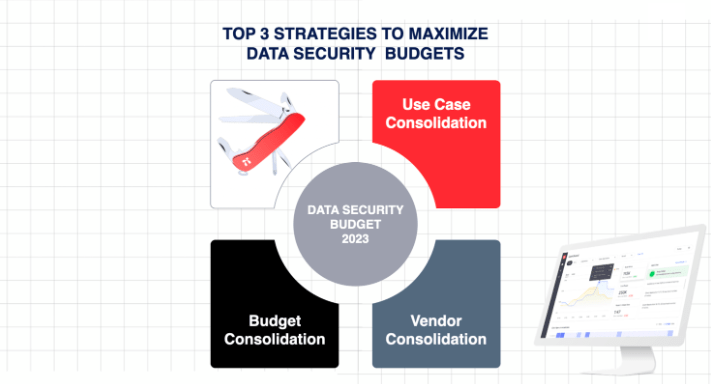
CISO Guide: 3 Strategies to Maximize Cybersecurity Budgets for Data Security
CISO Guide: 3 Strategies to Maximize Cybersecurity Budgets for Data Security This edition of Portal26’s Data Security Blog is dedicated to optimizing cybersecurity budgets as they relate to securing enterprise data . With the economic forecast being gloomy and waves of budget cuts as well as layoffs, it has become more challenging than ever before […]
CISO Guide: 3 Strategies to Maximize Cybersecurity Budgets for Data Security Read More »